In this post, we discuss options for regaining access to an AWS root account, even in the face of numerous challenges!
Bob Left the Company on Bad Terms
It happens. One day, the company’s cloud guru exits the company, voluntarily or involuntarily, for new pastures. Bridges are burned, communication channels are severed, and LinkedIn connections are removed. And then…
We need access to the AWS Root Account.
“No biggie! We have access to the root email address, so we can just request a password reset. Right?” But wait, “There is an MFA device added! Bob’s phone number is set! Do we have any access to the account??”
Let’s explore the various scenarios and options available to you in order to restore and recover access to the root user account.
Scenario – We have access to the root email account inbox.
Great! This one is easy, head over to the AWS Console and select the option to logon as the root user with the relevant root user email address.
Select the option “Forgot password?” as highlighted below. A password reset link will be emailed to the root email account, so that you can set a new password!
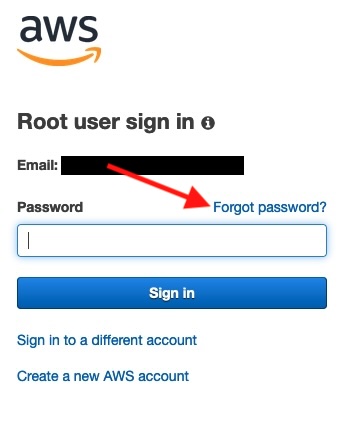
Scenario – We don’t have access to the root email account inbox.
In this scenario you don’t have access to the root email account inbox, and cannot recreate it. For example, the root email account is set to bob@gmail.com rather than your company domain e.g. bob@company.com. Bob isn’t available or helping, but you still need to regain access to the root account.
In this scenario you will need to engage AWS Support and your AWS Account Manager for support. You will be asked to provide details about the account in order to verify you are the owner, so expect to be asked for information such as billing addresses, payment information and several other security related questions. Once the details are verified then AWS support will guide you through recovering access and changing the root email address.
It will be a requirement that your contact details and phone number is set on the AWS Account. If not then don’t panic. We cover how to achieve this in a scenario below!
Scenario – An MFA device is set, that we no longer have access to.
In this scenario, an MFA device is enabled on the root user. For example, Bob configured an MFA on his personal phone authentication application. Maybe the MFA app. was on that company phone that was taken back and wipe… Give Bob a call to see if he will help, but if not then you can proceed as follows.
Head over to the AWS Console and select the option to logon as the root user with the relevant root user email address. Enter your root password and you will be presented with the Multi-factor authentication page, in which you will see a “Troubleshoot MFA” option as highlighted below:
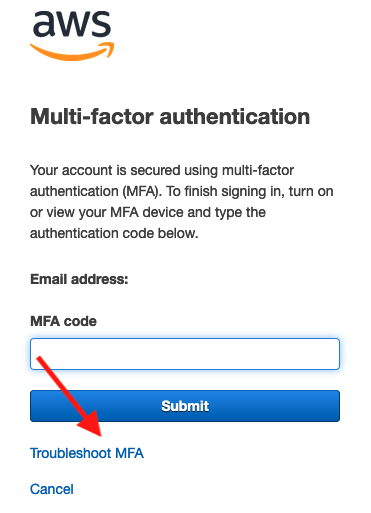
Select the option to “Sign in using alternative factors” and you will be presented with a verification page. Firstly, proceed with the “Email address verification” and you will be emailed a unique link. Once this is processed, you will then be able to proceed to “Phone number verification” in which a 6-digit code will be verified.
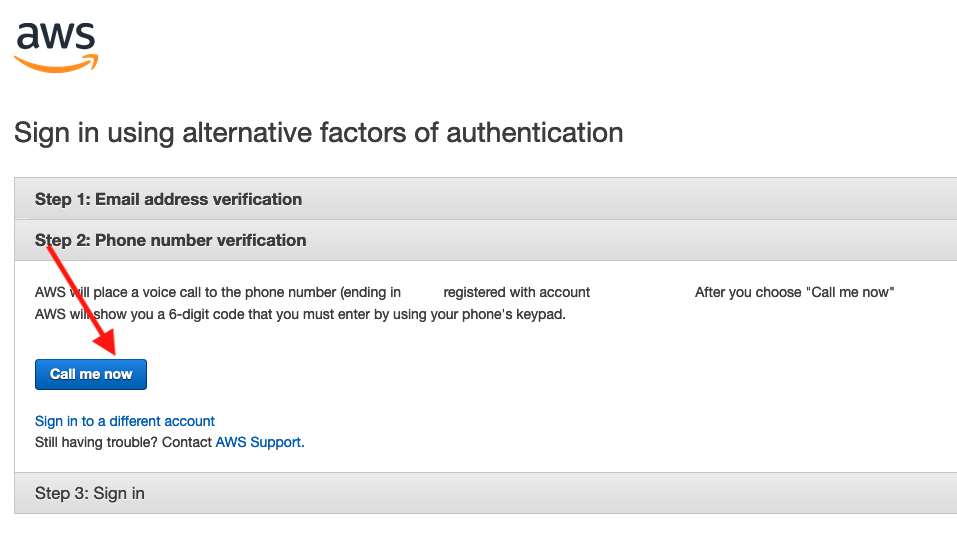
Note – For this verification to work, your phone number must be set as the primary contact number on the AWS Account. If you need to set the correct phone number, for example change it from Bob’s phone number, then please see scenarios below.
Scenario – An unknown or incorrect phone number is set on my AWS Account
In this scenario, an unknown or incorrect phone number is set on the AWS Account primary Contact Information. For example, Bob’s personal mobile number is set.
This raises some challenges, particularly if you are trying to perform the Phone number verification mentioned above… as the verification call will go to Bobs phone as oppose to your phone number. But, you have options to resolve this.
If you have an IAM Administrator user configured within the AWS Account, head over to the Account Settings Page and edit the Contact Information… adjusting the Phone number to one of your choosing. At that stage, continue with restoring access to your account using the email and phone verification methods already covered above.
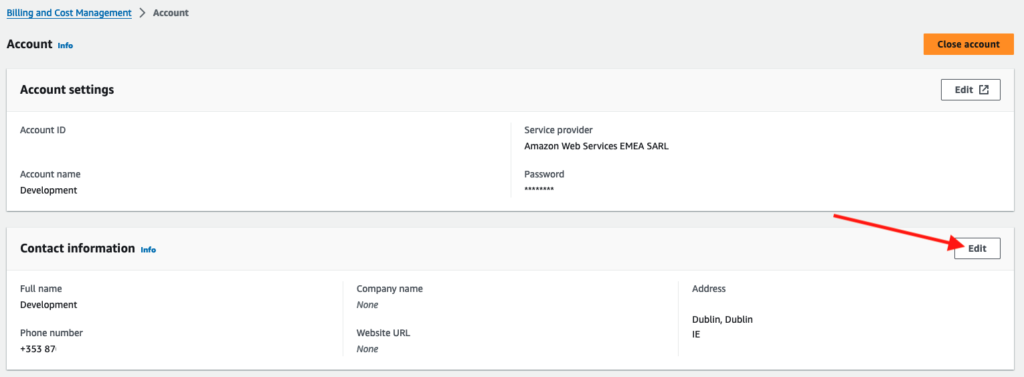
In order for this to work, “IAM User and Role Access to Billing Information” needs to be enabled on the AWS Account in question:
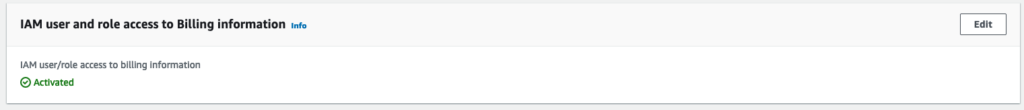
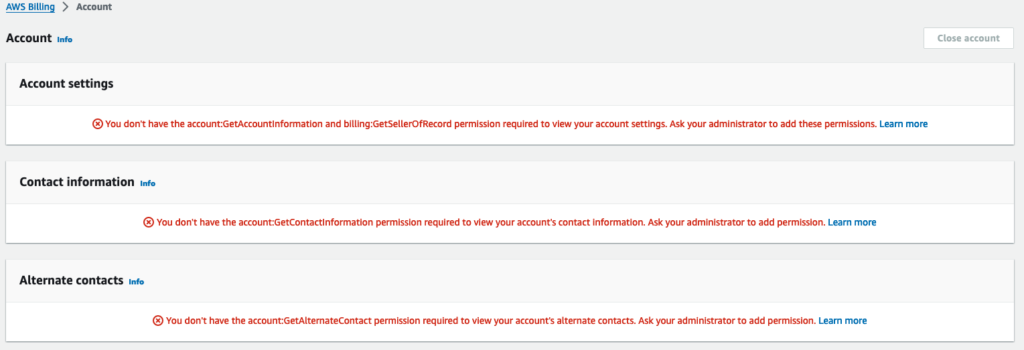
If it is not enabled, then you will start seeing errors messages similar to below, even if you have full IAM Administrator Access!
“You don’t have the account:GetContactInformation permission required to view your account’s contact information. Ask your administrator to add permission.”
The tricky part about this scenario is, in order to enable“IAM User and Role Access to Billing Information” you need to logon as the root user. So at this stage you may be in despair, thinking that you are blocked in proceeding. i.e.
- I can’t logon as the root user, as the current MFA device is unavailable
- Removing the MFA is not possible, as an incorrect phone number is configured so the phone verification method wont work
- I can’t change the phone number, as “IAM User and Role Access to Billing Information” is disabled. I need to logon as root to change that setting, but…
- I can’t logon as the root user, as the current MFA device is unavailable…(Infinite Loop)
Well, fear not!
You can actually change the phone number from the CloudShell! Even when IAM User and Role Access billing set to disabled*!
(*Correct as of May 2024… Expect AWS to fix this loophole at this some stage.)
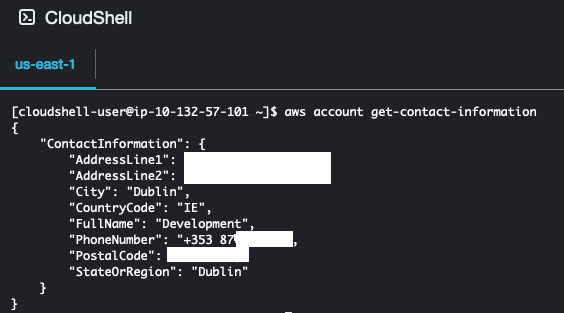
Head over to the AWS CloudShell within the account, and execute the following command as an IAM Administrator. Ensure to adjust the Contact Information to your own correct details!
aws account put-contact-information --contact-information AddressLine1='Building123',AddressLine2='Dublin Road',City='Dublin 4',CompanyName='CloudExplore',CountryCode=IE,FullName='Joe Bloggs',PhoneNumber=+353871234567,PostalCode='D04 ABCD',StateOrRegion=N/ATo verify the details have been updated, execute the following command from AWS CloudShell command: aws account get-contact-information
Scenario – I don’t have IAM AdminUser available to adjust the contact number
In this scenario, there are no privileged IAM users within the Account. For example, Bob was just managing and configuring the Account with the Root User.
Bad Bob! That’s not good practice…
Now it is getting tricky, but you may still have a few options depending on your AWS Account setup and in particular your AWS Organizations setup.
OrganizationAccountAccessRole
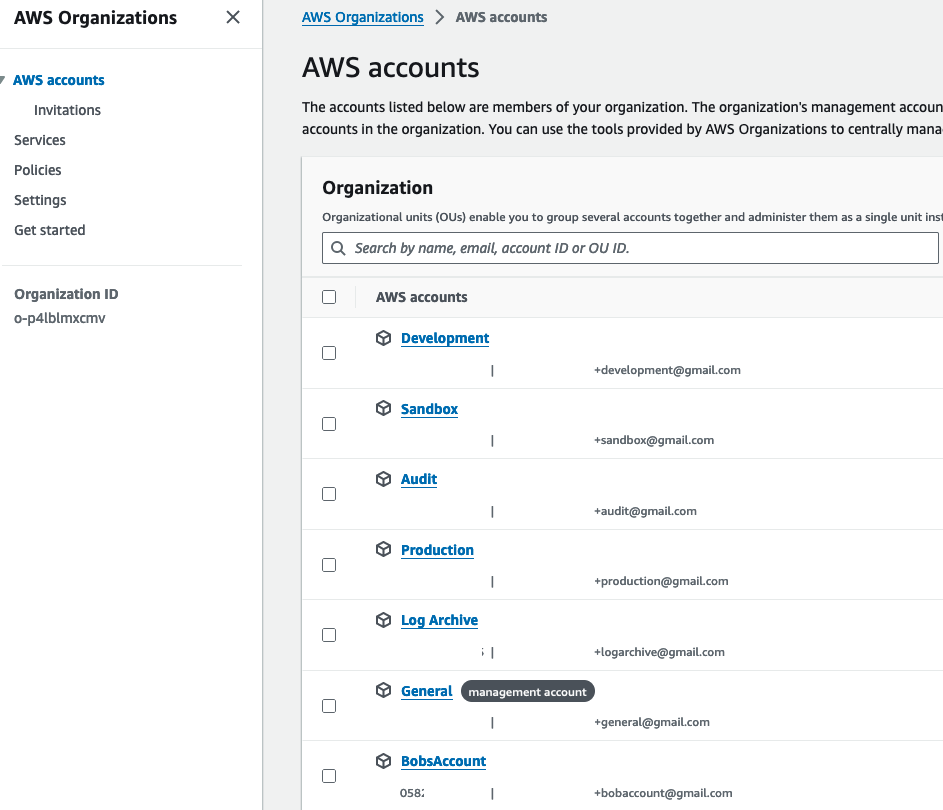
If the AWS Account which you are trying to recover access to is a member of an AWS Organization, there is a good chance a cross account access role has been created during the invite process. Access the Management Account of your AWS Organization, and browse to the AWS Organizations Service.
Within AWS Organizations, review the AWS Accounts list to see if Bobs Account is list. In the image below, I can see BobsAccount starting with Acc. ID 058…
From the Management Account, select “Switch Role” entering Bob’s Account ID and the IAM role name OrganizationAccountAccessRole.
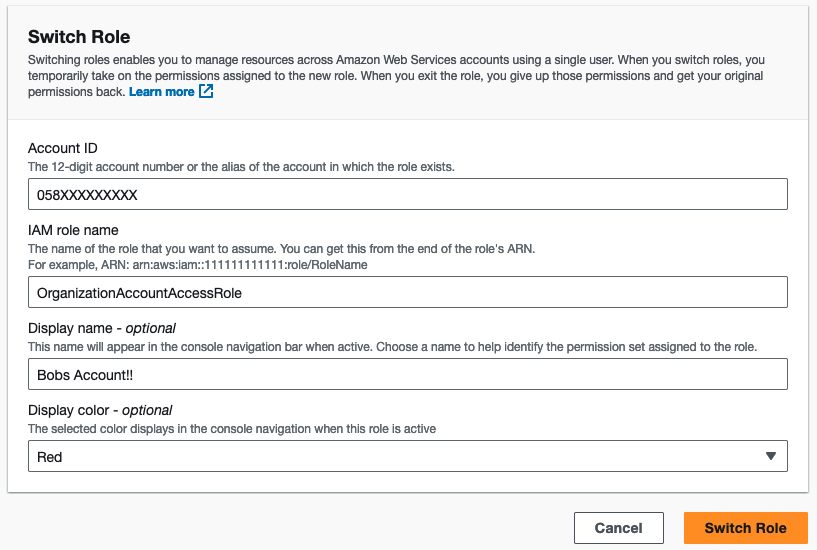
Providing the role was created when Bob’s Account was invited to the AWS Organization, you should be able to assume the role within Bob’s Account. From there create an IAM Adminstrator User within for performing the recovery steps covered above.
IAM Identity Center
In some scenarios, the OrganizationAccountAccessRole may not be available within the Member Account i.e. The role was deleted to improve security posture. If this is the case, you have an option to assume access within the Member Account using AWS IAM Identity Center, providing Bob’s Account is a member of your AWS Organization.
Access the Management Account of your AWS Organization, and browse to the IAM Identity Center service. Enable IAM Identity Center in a region of your choice, if it is not already enabled.
- Add a new user as outlined here.
- Add an IAM Administrator permission set as outlined here.
- Browse to the AWS Accounts within IAM Identity Center, and assign the user (created in step 1) and permission set (created in step 2) on the specific AWS Account as outlined here.
- Browse to the AWS SSO Access Portal URL, detailed on the IAM Identity Center Dashboard Landing Page. Logon as the new IAM Identity User (created in Step 1).
- Either use that IAM Identity User to perform the required tasks e.g. Change the phone number, or alternatively create a new IAM Administrator user within the account for performing any further actions.
I have exhausted all options
If you have attempted the above options and yet still cannot gain access to the root account, then the recommendation is to engage AWS Support and your AWS Account Manager for support. You will be asked to provide lots of details about the account in order to verify you are the owner, and this may be a lengthy process so patience will be required!
References
Resetting a lost or forgotten root user password
What if an MFA device is lost or stops working?
How do I update my telephone number to reset my lost MFA device?
Accessing member accounts in your organization
Switching to a role (console)
IAM Identity Center Documentation
About
With over 20 years in the technology sector, Keith has spent the last decade providing consultancy, support, and strategic direction to customers across multiple cloud platforms.





Disclaimer: The information shared on this blog is for informational purposes only and should not be considered as professional advice. The opinions presented here are personal and independent of any affiliations with tech companies or organizations.

